Jan 10, 2025
BitsLab's ScaleBit Security Team Discovers a Zero-Day Vulnerability Capable of Transferring All Assets from Uniswap Wallet
In October 2024, the ScaleBit Security Team, part of BitsLab, identified a vulnerability in the Uniswap iOS wallet, which was named “Unauthorized Access to Mnemonic Phrases”. This flaw enables attackers with physical access to a device to bypass the wallet’s authentication mechanisms and directly retrieve mnemonic phrases stored on the device.
This vulnerability implies that anyone with access to an unlocked device can extract the wallet’s mnemonic phrases in under three minutes. In everyday scenarios, temporarily lending a phone is not uncommon, especially among couples or friends. However, under the impact of this vulnerability, such seemingly innocuous actions could lead to the unintended exposure of wallet mnemonic phrases.
1.Background Information
Mnemonic phrases are critical credentials in the blockchain ecosystem, enabling access to and management of on-chain assets. Their exposure can lead directly to the loss of user funds. The discovery of this vulnerability highlights significant security weaknesses in the user authentication processes and key storage mechanisms of certain wallets.
It is worth noting that this vulnerability remains unaddressed in the latest version of the Uniswap Wallet available on the App Store (Version 1.42). We strongly advise all Uniswap Wallet users to remain vigilant and avoid lending their devices to others to prevent potential threats to their asset security. Additionally, users should closely monitor updates to the Uniswap Wallet and promptly install any patched versions.
We deeply understand the potential security risks this issue poses to user assets. Since October of last year, we have repeatedly urged the Uniswap team to address the issue, but our concerns have not received the attention they deserve. Therefore, we have decided to publicly disclose this vulnerability to raise awareness among users and developers about its severity and to encourage stronger security practices.
We firmly oppose any form of malicious exploitation and remain committed to providing professional security audits to safeguard the healthy development of the blockchain ecosystem.
2.Vulnerability Analysis
2.1 In similar products such as Metamask and Unisat wallets, mnemonic phrases are typically encrypted using symmetric encryption algorithms like AES-256-CBC. However, in the authentication process of the Uniswap Wallet, likely aiming to enhance user experience, only FaceID verification is provided. Users can access the wallet, initiate transactions, or view mnemonic phrases after FaceID authentication, without being prompted to enter a password.
This indicates that mnemonic phrases are either stored without encryption or encrypted using a fixed key. Upon reviewing the source code, it was confirmed that no effective encryption measures were applied during the storage of mnemonic phrases.
In this implementation, mnemonic phrases are stored in the Keychain via the keychain.set method without any additional encryption measures. Although iOS Keychain provides certain underlying encryption and access control mechanisms, such as accessibleWhenUnlockedThisDeviceOnly, these protections primarily rely on system-level security features rather than application-level encryption. As a result, they are insufficient to fully ensure the security of mnemonic phrases.
2.2 When users uninstall the wallet application directly, the mnemonic phrases stored on the device are neither deleted nor encrypted. However, the FaceID verification toggle within the wallet is reset, further compromising security.
2.3 Uniswap Wallet supports encrypting mnemonic phrases and uploading them to iCloud, as well as recovering them from iCloud. Additionally, the app provides a recovery page. When in recovery mode, the application retrieves and displays a list of mnemonic phrases available for recovery.
However, the conditions for triggering recovery mode are not limited to retrieving mnemonic phrases from iCloud. When the number of locally stored mnemonic phrases exceeds one, the recovery page is also displayed. In this scenario, the application may inadvertently expose multiple unencrypted mnemonic phrases.
This design creates a convenient attack vector for malicious actors. However, even without recovery mode, the core issue of storing mnemonic phrases unencrypted remains. Attackers could leverage other methods to directly extract unencrypted mnemonic phrases stored on the device. Such methods typically require more advanced exploitation conditions, such as jailbreaking the device to gain full access to system files or sideloading a modified application.
The unencrypted storage of mnemonic phrases thus serves as a critical entry point for potential attacks. Ensuring that mnemonic phrases are stored locally with robust encryption is essential to preventing the leakage of sensitive information.
3.PoC
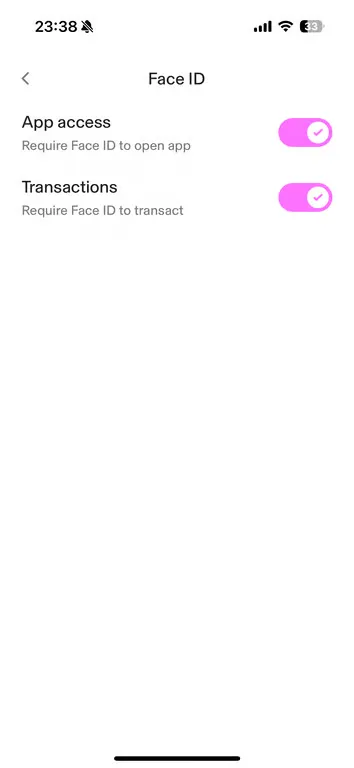
3.1 Install the Uniswap Wallet, Create a Wallet, Enable All Authentication Settings.
Record the Wallet’s Mnemonic Phrase:
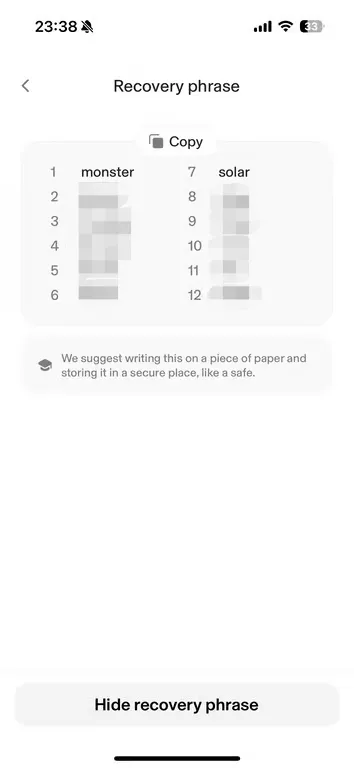
Enable All Authentication Settings:
3.2 Uninstall and Reinstall the Uniswap Wallet, Create a New Wallet.
3.3 Uninstall the wallet once more and reinstall it.
At this stage, the conditions to trigger the OnDeviceRecovery page are met, as the number of mnemonic phrases stored on the device exceeds one.
Upon entering recovery mode, the wallet displays the Recovery Page, revealing all previously stored unencrypted mnemonic phrases from the device.
This process exposes the user’s mnemonic phrases, demonstrating a significant design flaw in the Uniswap Wallet’s handling of mnemonic storage and recovery mechanisms.
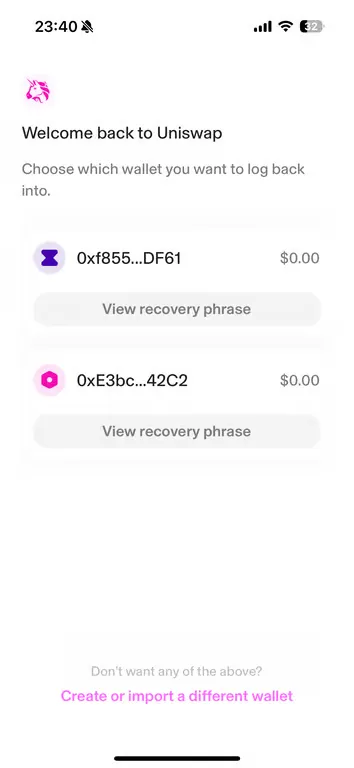
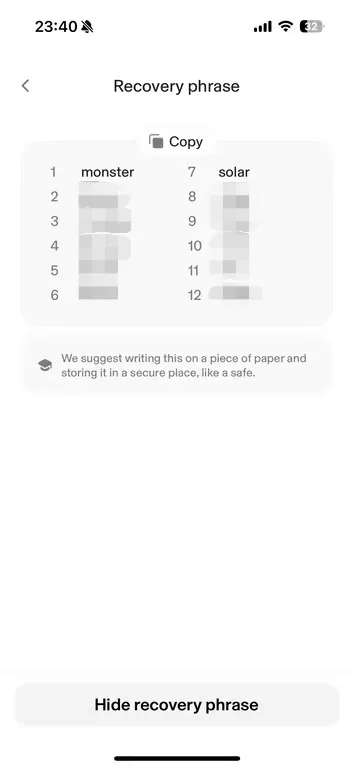
3.4 Verify one of the mnemonic phrases retrieved in recovery mode and confirm that it matches the mnemonic phrase created during the first wallet setup.
4.TimeLine
The vulnerability was submitted via Cantina on October 21, 2024. On November 28, 2024, the project team responded that while exploiting the vulnerability requires physical access to an unlocked device, the Likelihood might be downgraded, but the Impact remains high. They stated plans to confirm the issue and propose a solution. On December 5, 2024, the project team further replied that this was a known issue and refused to offer any reward.
The timeline is as follows:
October 21, 2024: The vulnerability was submitted via Cantina.
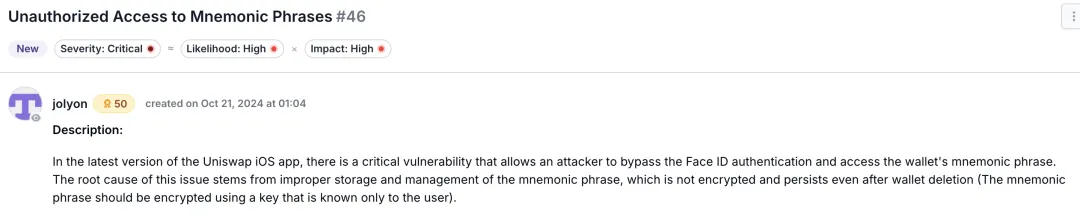
November 28, 2024: The project team acknowledged the impact and planned to propose a solution.

December 5, 2024: The project team stated that the vulnerability was already known and refused to provide a bounty.
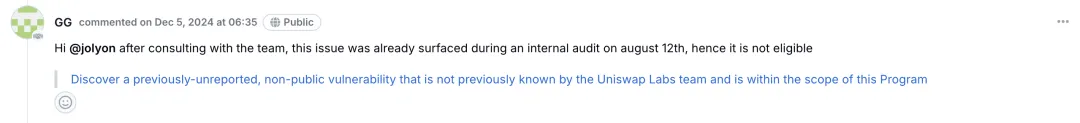
We reached out to the Uniswap team on December 18, 2024, and January 2, 2025, repeatedly urging them to address this issue promptly or disclose it to users. However, we received no response.
We firmly believe that users have the right to be informed about potential security risks to their assets. Given that this vulnerability has remained unpatched and users are unaware of it, we have decided to disclose the issue publicly. We informed the Uniswap team of our disclosure plan one week ago.
5.5.Summary
The root cause of this vulnerability lies in flawed design choices in the storage and access mechanisms for mnemonic phrases. The mnemonics are not effectively encrypted at the application layer, and the unreasonable conditions for triggering the recovery page allow attackers with physical access to a device to bypass the wallet’s authentication mechanism and directly retrieve the wallet’s mnemonic phrases.
This vulnerability persists in the latest version of Uniswap Wallet (Version 1.42), posing a potential risk to all users of the wallet. Therefore, users must take extra precautions to secure their devices physically, avoid disclosing unlock passwords, and refrain from lending their devices to others.
This incident also highlights the importance of prioritizing user asset security when designing wallet applications. Mnemonic phrases, as critical credentials for accessing and managing on-chain assets, must be adequately protected. Developers are advised to implement robust encryption at the application layer, such as encrypting mnemonic phrases using AES-256-CBC, and deriving encryption keys with user passwords via PBKDF2 or Argon2.
At the same time, ordinary users should enhance their security awareness by properly safeguarding their mnemonics, choosing wallets that have undergone rigorous security audits, and ensuring that these wallets implement strong encryption and robust security mechanisms. Users should avoid using wallets with unverified or unknown security standards to manage their assets.
Through this disclosure, we aim to raise awareness among developers and users about wallet security. Only through collaborative efforts—developers strengthening security designs, users improving security practices, and security teams contributing technical expertise—can we build a safer and more reliable blockchain ecosystem.
